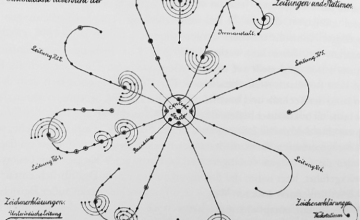
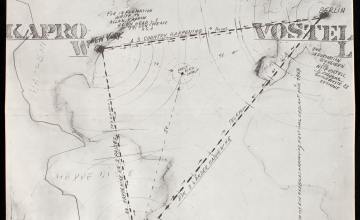
Chronological List of Network Experiments in Other Networks: A Radical Technology Sourcebook
I recently posted the table of contents and a chronological list of network entries that will appear in Other Networks: A Radical Technology Sourcebook. As I try to make clear in the introduction, most entries also include examples of experiments with or on these networks because we often don’t know just how compelling a given […]
Read More…